What is phishing?
‘Phishing’ is an attempt by criminals to uncover personal information, through pretending to be something/someone else. The objective of phishing is often to make the user visit a breached website, make a false payment (to the criminal in question) or lure the user into a false sense of security, with the user providing their personal information willingly.
What are the most common forms of phishing?
Google Docs
We have seen many clients fall victim to the “Google Docs” phishing scam, as it’s a tricky one to lookout for. These emails are highly targeted, often using emails and names associated with someone you may know, making it more likely for the user to assume its legitimate.
It encourages users to click on the “Open in Docs” link to view a shared document. However, at this point, the user will be redirected to a fake Google login page – despite looking the exact same. Once the user has entered their login details, the scammer will be granted access to the entirety of the Google Docs account.
Phishing through Google Docs doesn’t end there, however. More recently, scammers have been utilising the “comments” feature of Google Docs to target unsuspecting victims. In this particularly devious campaign, the attacker will add a comment to a Google document and mention the victim via their email address. What they can’t see, before they open the comment, is that the full comment includes a malicious link that triggers a malware infection of the targeted device.
Fake invoice
55% of money lost to scammers between December 2021 and February 2022 was lost through invoice scams. With SMEs (small and medium enterprises) losing an average of £2,100 to invoice scams.
It says it in the name, but it really isn’t as obvious as it seems. Scammers submit an invoice, or any other request for payment, in a very realistic fashion, to get you to send money to them. This is a very popular form of phishing – and you need to be alert of all invoices in your inbox. Attackers will often masquerade as invoicing platforms, such as Xero, Quickbooks or Sage, but have also been known to forge B2B invoices.
Spear phishing
Spear phishing is a generic term for a very sophisticated, accurate type of scam. Usually these are precise emails targeted towards a single person/type of person. Attackers will already have some personal information about the recipient, such as:
- Their name
- Place of employment
- Job title/info about what they do in their role
- Email address
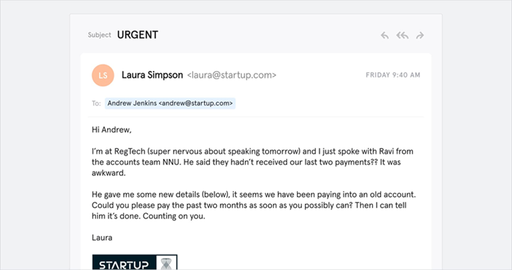
As you can imagine, knowing a lot of information about a particular person allows the attacker to make their phishing scam even more believable. The example below shows how convincing these attacks can be, once the scammer has information regarding the victim’s job role and colleagues.
Remember, always take the time to step back and reflect on an email. Is this request reasonable? Have you had similar requests in the past? If you’re unsure, reach out to your colleagues for confirmation before actioning anything. It’s always better to be on the side of caution.
Social media (angler phishing)
You and I both knew this was coming. The presence of social media in our current day and age is impossible to ignore. However, for all the good it does in bringing us closer together, unfortunately there will always be the few that utilise whatever means necessary to exploit others. Angler phishing is a technique used by scammers to act as false representatives of businesses online, often to trick dissatisfied customers into revealing personal details.
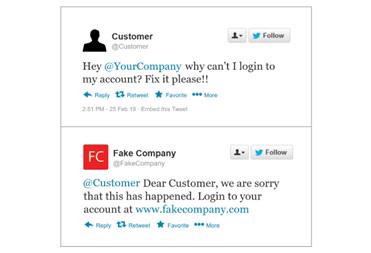
Image: BlueLoop
The state of phishing within organisations
A study conducted in 2021 by cybersecurity training and phishing simulation company KnowBe4 found that one in three untrained users were likely to fall for phishing or social engineering scams.
The report analysed businesses in a variety of industries to build what KnowBe4 calls an organization’s “phish-prone percentage (PPP),” which indicates how many employees are vulnerable to such attacks. The average baseline, 31.4%, varied greatly by organization size and industry.
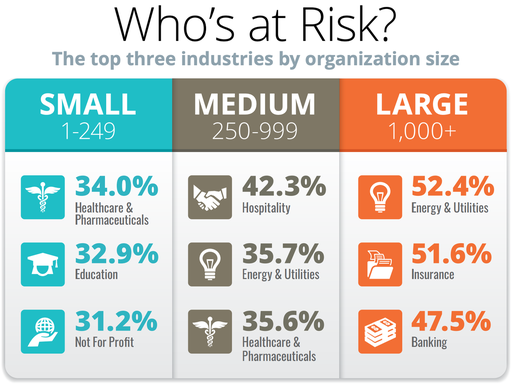 Image: KnowBe4
Image: KnowBe4
In the UK alone, the data looks slightly more promising. However, these percentages had risen from the year below. The reason being that inertia and the need to move large numbers of employees to remote working during the pandemic opened the door to cyber-attacks under a less protective and regulated business environment. In fact, according to a report in March 2021 conducted by the UK Department for Digital, Culture, Media and Sport (DCMS), 83% of businesses and 79% of charities reported phishing attacks over the last year.
Image: KnowBe4
Things to look out for – remember, being suspicious won’t hurt!
The examples provided below cover the main elements to look out for. However, it should be noted that phishing scams are becoming smarter and smarter – as such, this is not an exhaustive list.
Key things to look out for:
- The message is sent from a public email domain – no legitimate organisation will send emails from an address that ends in something like @yahoo.com or @gmail.com (even Google! They use google.com).
- Misspelt domain name – such as @microsftonline.com or @paypol.com
- Broken English (language that doesn’t sound correct for the type of email it is)
- Link/attachments included in the email – if you have any second thoughts about the email, don’t click them!
- Shortened URL’s such as bit.ly or t.co – they use these to mask the actual URL
- Keep a look out for HTTP (no HTTPS) - as secure websites tend to be HTTPS.
- Peculiar @ (social media)
- No verified tick on social media (not always applicable, depends on the size of company you are expecting to hear from)
According to the National Cyber Security Centre, scams will often feature one or more of these tell-tale signs:
Authority – Is the message claiming to be from someone official? Criminals will often pretend to be important people or organisations to trick you into doing something they want.
Urgency – Are you told you have a limited time to respond? By threatening you, criminals hope to pressure you into falling for their scam.
Emotion – Does the message make you panic, fearful, hopeful, or curious? Criminals will often use emotive language to influence your decision making.
Scarcity – Is the message offering something in short supply, like concert tickets or medicine? Fear of missing out (FOMO) is utilised to elicit a response.
Current events – Are you expecting to see a message like this? Criminals will often exploit current news stories, big events, or specific times of year (tax season) to make their scam seem more relevant and genuine.
For more information, visit their site: https://www.ncsc.gov.uk/collection/phishing-scams/spot-scams
What to do if you suspect an email?
The NCSC (National Cyber Security Centre) has the power to investigate and remove scam email addresses and websites. We recommend reporting any scam emails that you receive to them, to allow them to investigate the website/email address and shut it down if necessary – preventing anyone else from being affected by the same email/call/text message.
Use the following email address to report potential phishing offences to: report@phishing.gov.uk. Either forward the email on to them or take a screenshot of the email.
Their advice:
- Forward them as many suspicious emails as you like
- Send them emails that feel suspicious, even if you’re not certain they’re a scam – they can check.
- Don’t click on any links in a suspicious email.
- You don’t need to forward them suspicious emails you find in your spam/junk folder.
If you think you’re the victim of a phishing attack or you’d like to learn more, visit their website.